存取控制¶
Airflow Webserver UI 的存取控制由 Flask AppBuilder (FAB) 處理。請閱讀其相關的安全性文件,以了解其安全性模型。
預設角色¶
Airflow 預設提供一組角色:Admin、User、Op、Viewer 和 Public。預設情況下,只有 Admin 使用者可以設定/變更角色的權限。然而,建議保持這些預設角色不變,而是讓 Admin 使用者在必要時建立具有所需權限的新角色。
Public¶
Public 使用者(匿名)沒有任何權限。
Viewer¶
Viewer 使用者具有有限的讀取權限
VIEWER_PERMISSIONS = [
(permissions.ACTION_CAN_READ, permissions.RESOURCE_DAG),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_DAG_DEPENDENCIES),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_DAG_CODE),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_DAG_RUN),
(permissions.ACTION_CAN_READ, RESOURCE_ASSET),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_CLUSTER_ACTIVITY),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_POOL),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_IMPORT_ERROR),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_DAG_WARNING),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_JOB),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_MY_PASSWORD),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_MY_PASSWORD),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_MY_PROFILE),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_MY_PROFILE),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_SLA_MISS),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_TASK_INSTANCE),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_TASK_LOG),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_XCOM),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_WEBSITE),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_BROWSE_MENU),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_DAG),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_DAG_DEPENDENCIES),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_DAG_RUN),
(permissions.ACTION_CAN_ACCESS_MENU, RESOURCE_ASSET),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_CLUSTER_ACTIVITY),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_DOCS),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_DOCS_MENU),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_JOB),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_SLA_MISS),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_TASK_INSTANCE),
]
User¶
User 使用者除了 Viewer 權限外,還具有額外權限
USER_PERMISSIONS = [
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_DAG),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_DAG),
(permissions.ACTION_CAN_CREATE, permissions.RESOURCE_TASK_INSTANCE),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_TASK_INSTANCE),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_TASK_INSTANCE),
(permissions.ACTION_CAN_CREATE, permissions.RESOURCE_DAG_RUN),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_DAG_RUN),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_DAG_RUN),
(permissions.ACTION_CAN_CREATE, RESOURCE_ASSET),
]
Op¶
Op 使用者除了 User 權限外,還具有額外權限
OP_PERMISSIONS = [
(permissions.ACTION_CAN_READ, permissions.RESOURCE_CONFIG),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_ADMIN_MENU),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_CONFIG),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_CONNECTION),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_POOL),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_PLUGIN),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_VARIABLE),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_PROVIDER),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_XCOM),
(permissions.ACTION_CAN_CREATE, permissions.RESOURCE_CONNECTION),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_CONNECTION),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_CONNECTION),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_CONNECTION),
(permissions.ACTION_CAN_CREATE, permissions.RESOURCE_POOL),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_POOL),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_POOL),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_PLUGIN),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_PROVIDER),
(permissions.ACTION_CAN_CREATE, permissions.RESOURCE_VARIABLE),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_VARIABLE),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_VARIABLE),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_VARIABLE),
(permissions.ACTION_CAN_DELETE, permissions.RESOURCE_XCOM),
(permissions.ACTION_CAN_DELETE, RESOURCE_ASSET),
(permissions.ACTION_CAN_CREATE, RESOURCE_ASSET),
]
Admin¶
Admin 使用者擁有所有可能的權限,包括授予或撤銷其他使用者的權限。Admin 使用者除了 Op 權限外,還具有額外權限
ADMIN_PERMISSIONS = [
(permissions.ACTION_CAN_READ, permissions.RESOURCE_AUDIT_LOG),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_AUDIT_LOG),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_TASK_RESCHEDULE),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_TASK_RESCHEDULE),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_TRIGGER),
(permissions.ACTION_CAN_ACCESS_MENU, permissions.RESOURCE_TRIGGER),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_PASSWORD),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_PASSWORD),
(permissions.ACTION_CAN_READ, permissions.RESOURCE_ROLE),
(permissions.ACTION_CAN_EDIT, permissions.RESOURCE_ROLE),
]
自訂角色¶
DAG 層級角色¶
Admin 可以建立一組僅允許檢視特定 DAG 的角色。這稱為 DAG 層級存取。在 DAG 模型表中定義的每個 DAG 都被視為一個 View,它具有兩個相關聯的權限(can_read 和 can_edit。can_dag_read 和 can_dag_edit 自 2.0.0 版本起已棄用)。有一個特殊的檢視稱為 DAGs(在 1.10.* 版本中稱為 all_dags),它允許角色存取所有 DAG。預設的 Admin、Viewer、User、Op 角色都可以存取 DAGs 檢視。
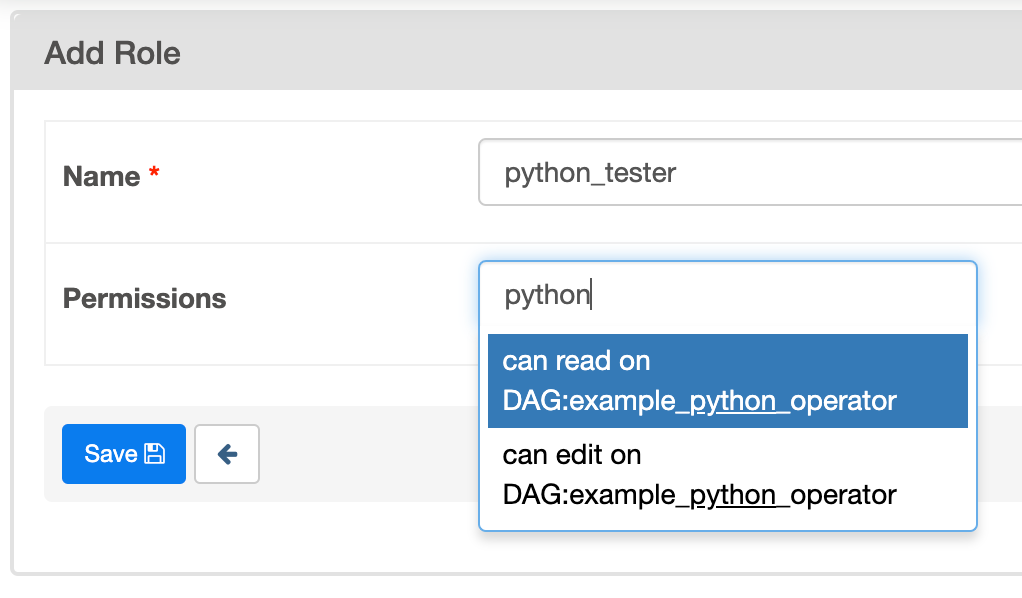
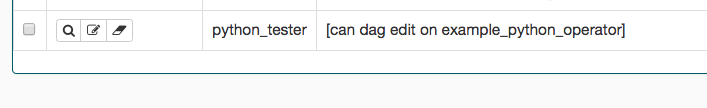
圖片顯示了如何建立一個只能寫入 example_python_operator 的角色。您也可以使用 CLI 透過 airflow roles create 指令建立角色,例如:
airflow roles create Role1 Role2
我們可以透過 airflow users add-role CLI 指令將指定的角色分配給新使用者。
權限¶
警告
Airflow 允許您為使用者定義具有細緻 RBAC 權限的自訂角色。但是,並非所有權限組合都完全一致,並且沒有機制可以確保分配的權限集完全一致。在許多情況下,特定資源的權限是重疊的。一個很好的例子是選單存取權限 - 缺少選單存取權限並不會自動停用對選單指向的功能的存取。另一個例子是對角色檢視的存取,即使使用者沒有「使用者檢視」存取權限,它也允許存取使用者資訊。當您沒有使用者存取權限時,新增角色存取權限是不一致的。
當您決定使用自訂的基於資源的權限集時,部署管理員應仔細檢查授予角色的最終權限集是否是他們期望的。
基於資源的權限¶
從 2.0 版本開始,權限基於個別資源以及對這些資源的一小部分操作。資源與標準 Airflow 概念相符,例如 Dag、DagRun、Task 和 Connection。操作包括 can_create、can_read、can_edit 和 can_delete。
然後將權限(每個權限都包含資源 + 操作對)新增至角色。
為了存取端點,使用者需要分配給該端點的所有權限
有五個預設角色:Public、Viewer、User、Op 和 Admin。每個角色都具有前一個角色的權限,以及額外的權限。
DAG 層級權限¶
僅對於 DAG 層級權限,可以在所有 DAG 或個別 DAG 物件層級控制存取權限。這包括 DAGs.can_read、DAGs.can_edit、DAGs.can_delete、DAG Runs.can_read、DAG Runs.can_create、DAG Runs.can_delete 和 DAG Runs.menu_access。當列出這些權限時,如果使用者具有列出的權限,或對正在操作的特定 DAG 具有相同的權限,則會授予存取權限。對於個別 DAG,資源名稱為 DAG: + DAG ID,對於 DAG Runs 資源,資源名稱為 DAG Run:。
例如,如果使用者嘗試檢視 example_dag_id 的 DAG 資訊,並且端點需要 DAGs.can_read 存取權限,如果使用者具有 DAGs.can_read 或 DAG:example_dag_id.can_read 存取權限,則將授予存取權限。
穩定 API 權限 |
|||
|---|---|---|---|
端點 |
方法 |
權限 |
最低角色 |
/config |
GET |
Configurations.can_read |
Op |
/connections |
GET |
Connections.can_read |
Op |
/connections |
POST |
Connections.can_create |
Op |
/connections/{connection_id} |
DELETE |
Connections.can_delete |
Op |
/connections/{connection_id} |
PATCH |
Connections.can_edit |
Op |
/connections/{connection_id} |
GET |
Connections.can_read |
Op |
/dagSources/{file_token} |
GET |
DAG Code.can_read |
Viewer |
/dags |
GET |
DAGs.can_read |
Viewer |
/dags/{dag_id} |
GET |
DAGs.can_read |
Viewer |
/dags/{dag_id} |
PATCH |
DAGs.can_edit |
User |
/dags/{dag_id}/clearTaskInstances |
PUT |
DAGs.can_edit, DAG Runs.can_edit, Task Instances.can_edit |
User |
/dags/{dag_id}/details |
GET |
DAGs.can_read |
Viewer |
/dags/{dag_id}/tasks |
GET |
DAGs.can_read, Task Instances.can_read |
Viewer |
/dags/{dag_id}/tasks/{task_id} |
GET |
DAGs.can_read, Task Instances.can_read |
Viewer |
/dags/{dag_id}/dagRuns |
GET |
DAGs.can_read, DAG Runs.can_read |
Viewer |
/dags/{dag_id}/dagRuns |
POST |
DAGs.can_edit, DAG Runs.can_create |
User |
/dags/{dag_id}/dagRuns/{dag_run_id} |
DELETE |
DAGs.can_edit, DAG Runs.can_delete |
User |
/dags/{dag_id}/dagRuns/{dag_run_id} |
GET |
DAGs.can_read, DAG Runs.can_read |
Viewer |
/dags/~/dagRuns/list |
POST |
DAGs.can_edit, DAG Runs.can_read |
User |
/assets |
GET |
Assets.can_read |
Viewer |
/assets/{uri} |
GET |
Assets.can_read |
Viewer |
/assets/events |
GET |
Assets.can_read |
Viewer |
/eventLogs |
GET |
Audit Logs.can_read |
Viewer |
/eventLogs/{event_log_id} |
GET |
Audit Logs.can_read |
Viewer |
/importErrors |
GET |
ImportError.can_read |
Viewer |
/importErrors/{import_error_id} |
GET |
ImportError.can_read |
Viewer |
/health |
GET |
None |
Public |
/version |
GET |
None |
Public |
/pools |
GET |
Pools.can_read |
Op |
/pools |
POST |
Pools.can_create |
Op |
/pools/{pool_name} |
DELETE |
Pools.can_delete |
Op |
/pools/{pool_name} |
GET |
Pools.can_read |
Op |
/pools/{pool_name} |
PATCH |
Pools.can_edit |
Op |
/providers |
GET |
Providers.can_read |
Op |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read |
Viewer |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances/{task_id} |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read |
Viewer |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances/{task_id}/links |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read |
Viewer |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances/{task_id}/logs/{task_try_number} |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read |
Viewer |
/dags/~/dagRuns/~/taskInstances/list |
POST |
DAGs.can_edit, DAG Runs.can_read, Task Instances.can_read |
User |
/variables |
GET |
Variables.can_read |
Op |
/variables |
POST |
Variables.can_create |
Op |
/variables/{variable_key} |
DELETE |
Variables.can_delete |
Op |
/variables/{variable_key} |
GET |
Variables.can_read |
Op |
/variables/{variable_key} |
PATCH |
Variables.can_edit |
Op |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances/{task_id}/xcomEntries |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read, XComs.can_read |
Viewer |
/dags/{dag_id}/dagRuns/{dag_run_id}/taskInstances/{task_id}/xcomEntries/{xcom_key} |
GET |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read, XComs.can_read |
Viewer |
/users |
GET |
Users.can_read |
Admin |
/users |
POST |
Users.can_create |
Admin |
/users/{username} |
GET |
Users.can_read |
Admin |
/users/{username} |
PATCH |
Users.can_edit |
Admin |
/users/{username} |
DELETE |
Users.can_delete |
Admin |
/roles |
GET |
Roles.can_read |
Admin |
/roles |
POST |
Roles.can_create |
Admin |
/roles/{role_name} |
GET |
Roles.can_read |
Admin |
/roles/{role_name} |
PATCH |
Roles.can_edit |
Admin |
/roles/{role_name} |
DELETE |
Roles.can_delete |
Admin |
/permissions |
GET |
Permission Views.can_read |
Admin |
網站權限 |
||
|---|---|---|
動作 |
權限 |
最低角色 |
存取首頁 |
Website.can_read |
Viewer |
顯示瀏覽選單 |
Browse.menu_access |
Viewer |
顯示 DAGs 選單 |
DAGs.menu_access |
Viewer |
取得 DAG 統計資訊 |
DAGs.can_read, DAG Runs.can_read |
Viewer |
顯示任務實例選單 |
Task Instances.menu_access |
Viewer |
取得任務統計資訊 |
DAGs.can_read, DAG Runs.can_read, Task Instances.can_read |
Viewer |
取得上次 DAG 執行 |
DAGs.can_read, DAG Runs.can_read |
Viewer |
取得 DAG 程式碼 |
DAGs.can_read, DAG Code.can_read |
Viewer |
取得 DAG 詳細資訊 |
DAGs.can_read, DAG Runs.can_read |
Viewer |
顯示 DAG 相依性選單 |
DAG Dependencies.menu_access |
Viewer |
取得 DAG 相依性 |
DAG Dependencies.can_read |
Viewer |
取得呈現的 DAG |
DAGs.can_read, Task Instances.can_read |
Viewer |
取得包含中繼資料的日誌 |
DAGs.can_read, Task Instances.can_read, Task Logs.can_read |
Viewer |
取得日誌 |
DAGs.can_read, Task Instances.can_read, Task Logs.can_read |
Viewer |
重新導向至外部日誌 |
DAGs.can_read, Task Instances.can_read, Task Logs.can_read |
Viewer |
取得任務 |
DAGs.can_read, Task Instances.can_read |
Viewer |
顯示 XCom 選單 |
XComs.menu_access |
Op |
取得 XCom |
DAGs.can_read, Task Instances.can_read, XComs.can_read |
Viewer |
建立 XCom |
XComs.can_create |
Op |
刪除 XCom |
XComs.can_delete |
Op |
觸發任務實例 |
DAGs.can_edit, Task Instances.can_create |
User |
刪除 DAG |
DAGs.can_delete |
User |
顯示 DAG 執行選單 |
DAG Runs.menu_access |
Viewer |
觸發 DAG 執行 |
DAGs.can_edit, DAG Runs.can_create |
User |
清除 DAG |
DAGs.can_edit, Task Instances.can_delete |
User |
清除 DAG 執行 |
DAGs.can_edit, Task Instances.can_delete |
User |
將 DAG 標記為封鎖 |
DAGS.can_edit, DAG Runs.can_read |
User |
將 DAG 執行標記為失敗 |
DAGS.can_edit, DAG Runs.can_edit |
User |
將 DAG 執行標記為成功 |
DAGS.can_edit, DAG Runs.can_edit |
User |
將任務標記為失敗 |
DAGs.can_edit, Task Instances.can_edit |
User |
將任務標記為成功 |
DAGs.can_edit, Task Instances.can_edit |
User |
以樹狀圖取得 DAG |
DAGs.can_read, Task Instances.can_read, Task Logs.can_read |
Viewer |
以圖表取得 DAG |
DAGs.can_read, Task Instances.can_read, Task Logs.can_read |
Viewer |
以持續時間圖表取得 DAG |
DAGs.can_read, Task Instances.can_read |
Viewer |
顯示所有嘗試 |
DAGs.can_read, Task Instances.can_read |
Viewer |
顯示著陸時間 |
DAGs.can_read, Task Instances.can_read |
Viewer |
切換 DAG 暫停狀態 |
DAGs.can_edit |
User |
顯示甘特圖 |
DAGs.can_read, Task Instances.can_read |
Viewer |
取得外部連結 |
DAGs.can_read, Task Instances.can_read |
Viewer |
顯示任務實例 |
DAGs.can_read, Task Instances.can_read |
Viewer |
顯示組態設定選單 |
Configurations.menu_access |
Op |
顯示組態 |
Configurations.can_read |
Viewer |
刪除多個記錄 |
DAGs.can_edit |
User |
將任務實例設定為執行中 |
DAGs.can_edit |
User |
將任務實例設定為失敗 |
DAGs.can_edit |
User |
將任務實例設定為成功 |
DAGs.can_edit |
User |
將任務實例設定為等待重試 |
DAGs.can_edit |
User |
自動完成 |
DAGs.can_read |
Viewer |
顯示資產選單 |
Assets.menu_access |
Viewer |
顯示資產 |
Assets.can_read |
Viewer |
顯示文件選單 |
Docs.menu_access |
Viewer |
顯示文件選單 |
Documentation.menu_access |
Viewer |
顯示工作選單 |
Jobs.menu_access |
Viewer |
顯示稽核日誌 |
Audit Logs.menu_access |
Viewer |
重設密碼 |
My Password.can_read, My Password.can_edit |
Viewer |
顯示權限選單 |
Permission Views.menu_access |
Admin |
列出權限 |
Permission Views.can_read |
Admin |
取得我的個人資料 |
My Profile.can_read |
Viewer |
更新我的個人資料 |
My Profile.can_edit |
Viewer |
列出日誌 |
Audit Logs.can_read |
Viewer |
列出工作 |
Jobs.can_read |
Viewer |
顯示 SLA 遺漏選單 |
SLA Misses.menu_access |
Viewer |
列出 SLA 遺漏 |
SLA Misses.can_read |
Viewer |
列出外掛程式 |
Plugins.can_read |
Viewer |
顯示外掛程式選單 |
Plugins.menu_access |
Viewer |
顯示供應商選單 |
Providers.menu_access |
Op |
列出供應商 |
Providers.can_read |
Op |
列出任務重新排程 |
Task Reschedules.can_read |
Admin |
顯示觸發器選單 |
Triggers.menu_access |
Admin |
列出觸發器 |
Triggers.can_read |
Admin |
顯示管理員選單 |
Admin.menu_access |
Viewer |
顯示連線選單 |
Connections.menu_access |
Op |
顯示集區選單 |
Pools.menu_access |
Viewer |
顯示變數選單 |
Variables.menu_access |
Op |
顯示角色選單 |
Roles.menu_access |
Admin |
列出角色 |
Roles.can_read |
Admin |
建立角色 |
Roles.can_create |
Admin |
更新角色 |
Roles.can_edit |
Admin |
刪除角色 |
Roles.can_delete |
Admin |
顯示使用者選單 |
Users.menu_access |
Admin |
建立使用者 |
Users.can_create |
Admin |
更新使用者 |
Users.can_edit |
Admin |
刪除使用者 |
Users.can_delete |
Admin |
重設使用者密碼 |
Passwords.can_edit, Passwords.can_read |
Admin |
這些 DAG 層級控制可以直接透過 UI / CLI 設定,或透過 access_control 參數編碼在 DAG 本身中。
DAG 層級權限的優先順序¶
由於 DAG 層級存取控制可以在多個位置設定,因此衝突是不可避免的,並且需要明確的解決策略。因此,Airflow 認為 DAG 本身提供的 access_control 參數如果存在,則具有完全的權威性,這會產生一些影響
在 DAG 上設定 access_control 將覆寫任何先前存在的 DAG 層級權限,如果它不是 None 的任何值
DAG(
dag_id="example_fine_grained_access",
start_date=pendulum.datetime(2021, 1, 1, tz="UTC"),
access_control={
"Viewer": {"can_edit", "can_read", "can_delete"},
},
)
也可以使用類似的方式新增 DAG Runs 資源權限,但需要明確新增資源名稱以識別權限適用於哪個資源
DAG(
dag_id="example_fine_grained_access",
start_date=pendulum.datetime(2021, 1, 1, tz="UTC"),
access_control={
"Viewer": {"DAGs": {"can_edit", "can_read", "can_delete"}, "DAG Runs": {"can_create"}},
},
)
這也表示設定 access_control={} 將從資料庫中清除給定 DAG 的任何現有 DAG 層級權限
DAG(
dag_id="example_no_fine_grained_access",
start_date=pendulum.datetime(2021, 1, 1, tz="UTC"),
access_control={},
)
相反地,從 DAG 中完全移除 access_control 區塊(或將其設定為 None)不會進行任何變更,並可能留下懸而未決的權限。
DAG(
dag_id="example_indifferent_to_fine_grained_access",
start_date=pendulum.datetime(2021, 1, 1, tz="UTC"),
)
如果 DAG 本身沒有定義 access_control,Airflow 將延遲到資料庫中定義的現有權限,這些權限可能是透過 UI、CLI 或先前在相關 DAG 上的 access_control 參數設定的。
在所有情況下,系統範圍的角色(例如 Can edit on DAG)優先於 DAG 層級存取控制,因此可以將它們視為 Can edit on DAG: *